ScanWorks Embedded Diagnostics
ScanWorks Embedded Diagnostics
With embedded JTAG-based run-control, information about difficult-to-reproduce failures in the field can be captured for analysis.
- Embed debug logic in the board to retrieve information for use in diagnosing failures that occur in the field
- Eliminate the need for external cables and hardware probes
- Provide 24×7 debug access to low-level hardware, firmware, silicon and software faults

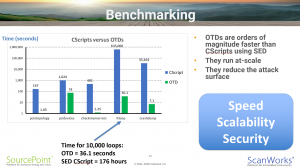
This comprehensive technical reference manual describes the API for programming On-Target Diagnostics directly down on the target service processor. Having the run-control API directly accessible on the target itself, as opposed to a remote host, provides more Speed (performance is significantly higher without the backhaul overhead), Scalability (the debug agent runs at-scale, down on the target), and Security (with a BMC at the root of trust, the data network backhaul is no longer an attack surface).
JTAG-based embedded In-Target Probe (ITP)
ScanWorks Embedded Diagnostics (SED) is a custom embedded ITP implementation that provides on target run-control via the Baseboard Management Controller (BMC) for target applications that require 5 nines or 6 nines reliability. In these applications, a failure must be analyzed without the actual plugging in of an ITP JTAG probe. This requirement implies that the software is already resident on the target and that an external processor (BMC) has the ability to conduct forensics on the hung server processor. Intel has implemented the ability for a crashed/hung processor to keep valuable postmortem information available within the CPU.
SED operates in two modes:
1. Run CScripts from a remote host connected to the failing server to extract this data prior to system reset.
2. Implement on-target diagnostics (OTD) using Python or C/C++ directly on the BMC.
SED’s architecture delivers superior:
1. Speed
2. Scalability
3. Security
versus alternative solutions.
ScanWorks Embedded Diagnostics for Test
JTAG/Boundary Scan tests are typically used “locally”, with the software running on an external PC that accesses a UUT through dedicated hardware.
ScanWorks Embedded Diagnostics (SED) for Test is an advanced tool strategy that supports implementing Built-In Test (BIT) for JTAG-based structural testing, programming, and debug functions – all running natively on existing UUT hardware. By embedding ASSET’s JTAG engine within an onboard service processor or FPGA on the UUT, the Boundary Scan test become part for the overall system.
The Boundary Scan vectors can used for Power-On Self Test (POST) and for in-situ debug/repair. The vectors can be used on the benchtop, in prototype, and in manufacturing test. SED for Test opens up a very powerful “remote” out-of-band Boundary Scan experience.
- No external cables or hardware needed to perform Boundary Scan test and debug functions
- Test and debug functions can be executed in-situ, as part of a Built-In Test (BIT), Power-On Self Test (POST), system audits, operational measurements, etc.
- Board just needs power; there is no requirement for the system to boot or be operational
- Provides a level of diagnostic granularity not usually found via in-system functional tests
- Out of band technology for dramatic reduction in No Fault Found (NFF) cost and system availability issues
- An innovative approach using a proven, mature technology
- SED for Test can be implement on a system-based to test across boards and backplanes
- Diagnostic data can be stored on board for download in the depot
- Same test can be run in-situ and on the benchtop, in prototype, manufacturing test, and debug and repair
- Addresses No Fault Found (NFF) and system availability issues